What are the protocols used in the transport layer?
- UDP stands for User Datagram Protocol.
- UDP is a simple protocol and it provides nonsequenced transport functionality.
- UDP is a connectionless protocol.
- This type of protocol is used when reliability and security are less important than speed and size.
What is protocol is used at the transport layer?
Services provided by the Transport Layer
- End-to-end delivery: The transport layer transmits the entire message to the destination. Therefore, it ensures the end-to-end delivery of an entire message from a source to the destination.
- Reliable delivery: The transport layer provides reliability services by retransmitting the lost and damaged packets. ...
- Flow Control. ...
- Multiplexing. ...
Why is PPTP an outdated and insecure protocol?
When NOT to use PPTP:
- Security is important
- You need stronger than 128-bit encryption
- Your ISP blocks VPN traffic
- Your VPN server is far away
- You have easy access to Alternative protocols
How to setup your own VPN with PPTP?
Set up Your Own PPTP VPN Server On Debian, Ubuntu, CentOS
- Install pptpd. Since the PPTP VPN daemon package is available in EPEL (Extra Package for Enterprise Linux) repository, we have to add the repository and then install pptpd.
- Adding DNS Servers. If Google’s DNS server is blocked in your area, then you can use OpenDNS Server: 208.67.222.222 and 208.67.220.220
- Adding VPN User Accounts. ...
Which encryption protocol does GRE?
GRE (generic Routing Encapsulation) uses IPsec for security when transmitting.
What kind of ticket is held by Kerberos TGS?
In Kerberos authentication, a Ticket Granting Ticket (TGT) is a user authentication token issued by the Key Distribution Center (KDC) that is used to request access tokens from the Ticket Granting Service (TGS) for specific resources/systems joined to the domain.
Which type of encryption is commonly used to secure VPNS quizlet?
IPsec provides authentication and encryption, and it can be used in conjunction with L2TP or by itself as a VPN solution.
Which protocol assigns a virtual IP to a group of routers?
In the case of routers, VRRP or HSRP is used to assign a virtual IP address to a group of virtual routers.
Which transport layer protocol does Pptp use quizlet?
Which Transport layer protocol does PPTP use? - PPTP (point-to-point tunneling protocol), is an older, Layer 2 protocol developed by Microsoft that encapsulates VPN data frames. It uses TCP segments at the Transport layer.
Which transport layer protocol does L2TP use?
Layer 2 Transport ProtocolThe Layer 2 Transport Protocol (L2TP) is another generic encapsulation protocol designed to allow you to tunnel IP networking.
What does PPTP use for encryption?
MPPEMicrosoft's PPTP uses MPPE to encrypt the data in a PPTP VPN, providing the security for the data that travels between the VPN client and server. Although PPTP itself can use any PPP authentication mechanism, MPPE requires encryption keys generated by MS-CHAP v1 or v2, or EAP-TLS.
What does PPTP use for encryption What does L2TP use?
As expected, PPTP is derived from the Generic Routing Encapsulation protocol (GRE) and Point-to-Point Protocol (PPP). As it is from Microsoft, the encryption is done via RC4-based Microsoft Point-to-Point Encryption. PPTP is often favored because it is easy to use and to set-up.
Do all tunneling protocols use encryption?
A tunnel is not encrypted by default: the TCP/IP protocol chosen determines the level of security. SSH uses port 22 to enable data encryption of payloads being transmitted over a public network (such as the Internet) connection, thereby providing VPN functionality.
What is the VRRP protocol used for?
The Virtual Router Redundancy Protocol (VRRP) is a computer networking protocol that provides for automatic assignment of available Internet Protocol (IP) routers to participating hosts. This increases the availability and reliability of routing paths via automatic default gateway selections on an IP subnetwork.
Is VRRP a layer 3 protocol?
VRRP is an election protocol that dynamically assigns the Virtual IP to one of the routers of the VRRP Group. The Routers operate in a local area network. the Updates are not forwarded beyond the local subnet. Hence it is a layer-2 protocol.
What is VRRP protocol in networking?
The Virtual Router Redundancy Protocol (VRRP) eliminates the single point of failure inherent in the static default routed environment. VRRP specifies an election protocol that dynamically assigns responsibility for a virtual router (a VPN 3000 Series Concentrator cluster) to one of the VPN Concentrators on a LAN.
What is the transport layer?
The transport layer is the center of the entire hierarchy of the protocol. Two protocols display the transport layer. 1.
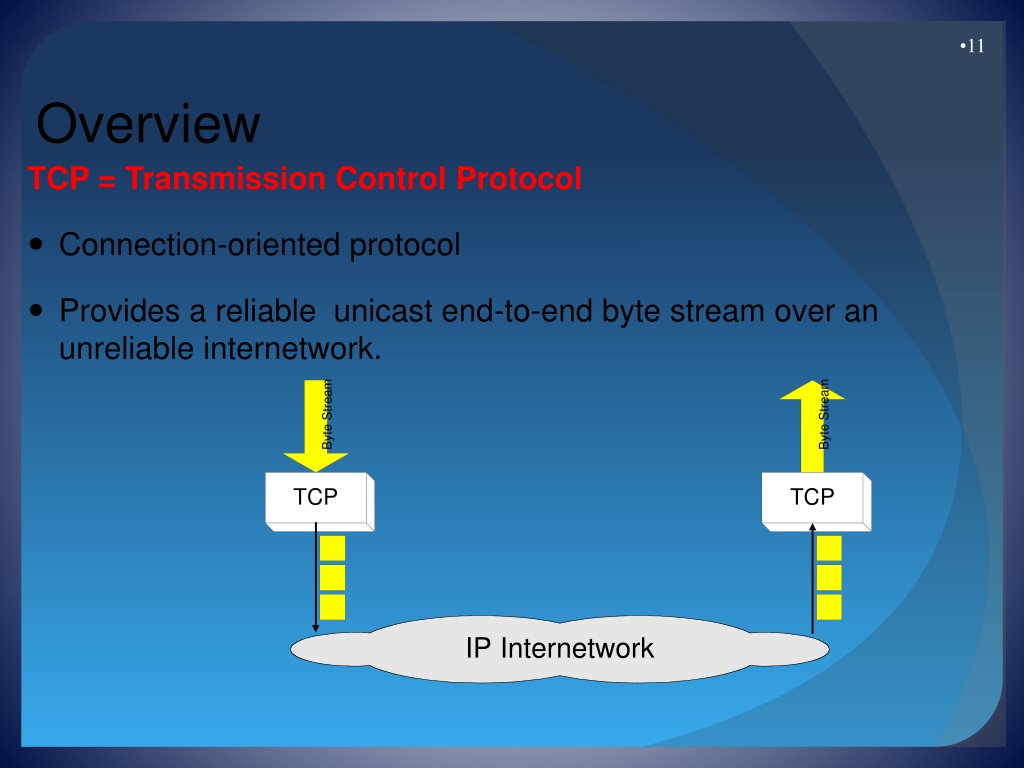
What is TCP protocol?
TCP is a protocol that specifies how network connections can be developed and maintained under which applications can share data. TCP uses the Internet Protocol (IP) to describe how computers transmit data packets to each other.
What are the features of TCP?
Features of TCP Protocol 1 Multiplexing: Multiplexing is a method of accepting and forwarding data on separate computers from various applications to each server. The data is sent to the right device at the receiver’s end. It is called demultiplexing. Through using the logical channels known as ports, TCP transmits the packet to the appropriate program. 2 Full Duplex: TCP offers Full Duplex operation, i.e. simultaneously data flux in both directions. Can TCP have buffers sent and received so that the segments can flow in both directions for full-duplex services? TCP is a protocol that binds. Assume that process A requires the data from process B to be sent and received. 3 Flow Control: Once TCP receives a data packet, it returns to the sender displaying the number of bytes without exhausting the internal buffer. In ACK, the number of bytes is sent as the highest sequence number, which it can easily obtain. It is also known as the window process 4 Logical Connections: A logical relation is called the combination of sockets, sequence numbers, and window sizes. The pair of sockets used by sending and receiving processes are used to classify each connection.
What is TCP multiplexing?
Features of TCP Protocol. Multiplexing: Multiplexing is a method of accepting and forwarding data on separate computers from various applications to each server. The data is sent to the right device at the receiver’s end. It is called demultiplexing.
What is connectionless and connection-oriented?
Connectionless and connection-oriented can exist for a transportation layer protocol. Every segment is treated as independent first packets and transported to the destination machine transport layer in connectionless.
Why does UDP not indicate which packet has been lost?
UDP can notice that there has been an error, but does not indicate which packet has been lost because it does not have an ID or a data sequence number.