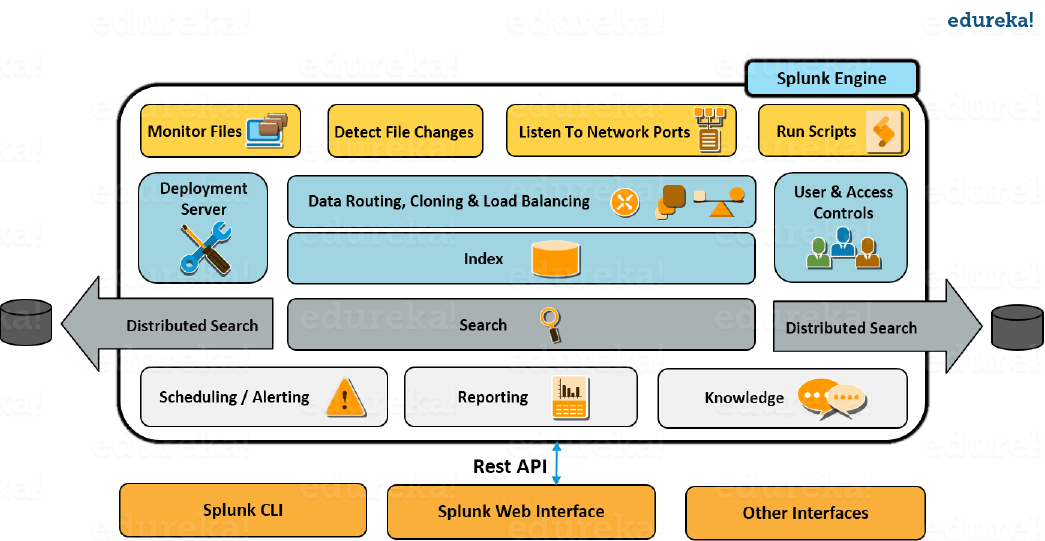
Splunk Architecture has the following three components:
- Splunk Forwarder: This is used to gather and forward the real-time data with less processing power
- Splunk Indexer: This is used for parsing and indexing data so that it is easy to perform search operations.
- Search Head: This is the user interface where the user can retrieve the data based on the keywords
What is Splunk and how does it work?
Splunk started out as a kind of “Google for Logfiles”. It does a lot more today but log processing is still at the product’s core. It stores all your logs and provides very fast search capabilities roughly in the same way Google does for the internet. Search Processing Language
What is Splunk used for?
What Is Splunk Used For? Splunk has become a popular choice for application management, security and compliance. It’s also used for business and web analytics. Because it simplifies the task of searching for specific data that is buried in massive amounts of more complex data, Splunk has become a go-to option for troubleshooting system failures.
What kinds of technologies does Splunk use?
What technology does Splunk use? Splunk is a horizontal technology used for application management, security and compliance, as well as business and web analytics. Recently, Splunk has also begun developing machine learning and data solutions for BizOps. Splunk. Type Public Website splunk.com
Which of these is not a main component of Splunk?
Which of these is not a main component of Splunk? Compress and archive. The index does not play a major role in Splunk. False. Data is broken into single events by: sourcetype. OTHER SETS BY THIS CREATOR. ISC2 - CAP. 328 terms. shabaaz3000. INFORMATION SECURITY INTERVIEW Q&A. 29 terms. shabaaz3000. NIST 800-53. 23 terms.
See more
What are Splunk Enterprise components?
Components of a Splunk Enterprise deploymentIndexer.Search head.Forwarder.Deployment server.Functions at a glance.Index replication and indexer clusters.
What is Splunk architect?
A Splunk Enterprise Certified Architect has a thorough understanding of Splunk Deployment Methodology and best-practices for planning, data collection, and sizing for a distributed deployment and is able to manage and troubleshoot a standard distributed deployment with indexer and search head clustering.
How many basic components are there in Splunk architecture Brainly?
1 Answer. Splunk Architecture has the following three components: Splunk Forwarder: This is used to gather and forward the real-time data with less processing power. Splunk Indexer: This is used for parsing and indexing data so that it is easy to perform search operations.
How many basic Splunk architecture are there?
There are 3 main components in Splunk: Splunk Forwarder, used for data forwarding. Splunk Indexer, used for Parsing and Indexing the data. Search Head, is a GUI used for searching, analyzing and reporting.
Which of the following is not a component of Splunk?
The correct answer is option B (compress and archive). Splunk tool provides us functionalities such as collecting and indexing data, allows us to analyze the data, and increase search capabilities also. Splunk does not have features to compress and archive data.
What is standalone architecture in Splunk?
A standalone deployment in Splunk means that all the functions that Splunk does are managed by a single instance. Various functions that a Standalone Deployment can do are: Searching. Indexing. Parsing.
What are 3 main components in a Splunk architecture?
Splunk Components. The primary components in the Splunk architecture are the forwarder, the indexer, and the search head.
What are the various roles in Splunk?
The predefined roles are: admin : This role has the most capabilities. power : This role can edit all shared objects and alerts, tag events, and other similar tasks. user : This role can create and edit its own saved searches, run searches, edit preferences, create and edit event types, and other similar tasks.
What are stages of Splunk indexing?
Event processing occurs in two main stages, parsing and indexing. All data that comes into Splunk Enterprise enters through the parsing pipeline as large (10,000 bytes) chunks. During parsing, Splunk Enterprise breaks these chunks into events which it hands off to the indexing pipeline, where final processing occurs.
Which component of Splunk has no GUI?
Which component should not have web gui? Search Head can not index the data.
What is the main use of Splunk?
Splunk is used for monitoring and searching through big data. It indexes and correlates information in a container that makes it searchable, and makes it possible to generate alerts, reports and visualizations.
What are Splunk search heads?
search head noun. In a distributed search environment, a Splunk Enterprise instance that handles search management functions, directing search requests to a set of search peers and then merging the results back to the user. A Splunk Enterprise instance can function as both a search head and a search peer.
What is the purpose of Splunk?
Splunk software explores, evaluates, and converts data during the Parsing phase to extract only the relevant data. It is also referred to as process automation. Splunk software splits the data stream into single events during this phase. The parsing phase is divided into several sub-phases:
Why is Splunk important?
Splunk processes incoming data to allow for quick search and analysis. It improves the data in a variety of ways, including:
What is Splunk indexer?
The indexer is the Splunk component that will be used to index and store the data from the forwarder. The Splunk instance converts incoming data into events and stores it in indexes for efficient search operations. If the data is received from a Universal forwarder, the indexer will first parse it before indexing it. Data parsing is used to remove unwanted data. However, if the data is received from a Heavy forwarder, the indexer will only index the data.
What is Splunk metadata?
Splunk software uses up the raw stream of data from its own origin, divides it into 64K blocks, and analyzes each block with metadata keys during this stage. The metadata keys also include data's hostname, source, and source type.The keys can also contain values being used internal and external, like the data stream's character encoding, and value systems that control data analysis during the indexing stage, like the index into which the events should be stored.
What is the Splunk search function?
Splunk application stores consumer knowledge objects, such as documents, event types, dashboards, alerts, and field extractions, as part of its search function. The search function is also in charge of managing the search process.
What is Splunk software?
With Splunk software, it is simple to search for specific data within a cluster of complex data. It is difficult to determine which configuration is currently active in log files. To clarify, the Splunk application employs a tool that assists the user in locating issues with a configuration file and viewing the current configurations that are in use.
What is the purpose of Splunk's indexing phase?
During the Indexing phase, Splunk software needs to write parsed events to a disk index. It saves both of the condensed raw data and the index file. The advantage of indexing is that the data is easily accessible during searching.
What are the components of Splunk?
The primary components in the Splunk architecture are the forwarder, the indexer, and the search head.
What is a splunk?
Splunk Big Data: a Beginner’s Guide. Splunk is a tool you can use to derive value from your big data. It enables you to incorporate insights from a variety of tools, allowing you to collect, search, index, analyze, and visualize your data from a central location.
Why use cluster indexers in Splunk Enterprise?
In Splunk Enterprise, you can set up a cluster of indexers with replication between them, to avoid data loss and provide more system resources and storage space to handle large data volumes.
How does Splunk work?
There are two main ways to use Splunk for data analytics—Splunk Enterprise that collects log data from across the enterprise and make it available for analysis, and Splunk Hunk that indexes and makes queries of Hadoop data, creates dashboards and reports directly from Hadoop datasets.
How does Splunk store logs?
Data Storage – Splunk parses log data, by breaking it into lines, identifying timestamps, creating individual events and annotating them with metadata keys. It then transforms event data using transformation rules defined by the operator. Finally, Splunk writes the parsed events to disk, pointing to them from an index file which enables fast search across huge data volumes.
What is data input in Splunk?
Data Input – Splunk ingests the raw data stream from the source, breaks it into 64K blocks, and adds metadata keys, including hostname, source, character encoding, and the index the data should be stored in.
What is a search head in Splunk?
The search head provides the UI users can use to interact with Splunk. It allows users to search and query Splunk data, and interfaces with indexers to gain access to the specific data they request.
What is a Splunk search?
In a Splunk instance, a search head can send search requests to a group of indexers, or search peers, which perform the actual searches on their indexes. The search head then merges the results and sends them back to the user. This is a faster technique to search data called distributed searching.
What is the search function in Splunk?
As part of the search function, Splunk software stores user-created knowledge objects, such as reports, event types, dashboards, alerts and field extractions. The search function also manages the search process.
How much CPU does Splunk Forwarder use?
Compared to other traditional monitoring tools, Splunk Forwarder consumes very less cpu ~1-2%. You can scale them up to tens of thousands of remote systems easily, and collect terabytes of data with minimal impact on performance.
What is Splunk indexer?
Indexer is the Splunk component which you will have to use for indexing and storing the data coming from the forwarder. Splunk instance transforms the incoming data into events and stores it in indexes for performing search operations efficiently.
What is metadata in Splunk?
In this stage, Splunk software consumes the raw data stream from its source, breaks it into 64K blocks, and annotates each block with metadata keys. The metadata keys include hostname, source, and source type of the data. The keys can also include values that are used internally, such as character encoding of the data stream and values that control the processing of data during the indexing stage, such as the index into which the events should be stored.
Can you download the Splunk tutorial series?
You can also download the Splunk Tutorial Series e-book.
Can you install search head on splunk?
You can install the search head on separate servers or with other Splunk components on the same server. There is no separate installation file for search head, you just have to enable splunkweb service on the Splunk server to enable it.
How robust is Splunk?
Splunk is an incredibly robust tool that can scale depending on the certain parameters: Number of users using the deployment, Amount of data coming in, Number of endpoints sending data to the deployment.
What is Splunk's indexer?
An indexer is used to index/parse the data. Splunk uses its proprietary algorithm to store the data in a way that it can be retrieved in a faster manner and then searched upon.
Can Captain Nodes manage Splunk?
Supportaibility is challenging, however, with Master and Captain Nodes we can manage the Splunk configs and apps easily
Is Splunk a standalone application?
There are a few drawbacks of a “Standalone” deployment for Splunk in terms of High Availability, Disaster Recovery and Search Concurrency. To overcome some of these, Splunk can be set up in a way to distribute the tasks to different instances within the platform.
What is a splunk?
Splunk is a well-developed and advanced software tool designed for organizations to perform indexing and searching log files stored in a system. It analyzes machine-generated data in real-time. It also searches, monitors, and examines machine-generated data via a web-style interface. Apart from examining machine-generated data it also captures, indexes, and correlates the real-time data in a searchable container from where they are produced in the form of graphs, reports, alerts, dashboards, and visualizations for diagnosis and provide various solutions to the business problems.
What is a Splunk Cloud?
Splunk Cloud: Splunk Cloud is the hosted platform provided as a service with subscription pricing. The features included in this package are similar to the Splunk enterprise version. In the architecture, clustering is managed by Splunk.
How many MB is Splunk Light?
Splunk Light: Splunk light is the free version with up to 500MB indexing per day . In this version, the features and functionalities are limited as compared to other versions. The architecture supports only a single instance.
How many types of Splunk forwarders are there?
There are 2 different types of Splunk forwarder in Splunk Architecture:
What is indexer in Splunk?
Indexer: The indexer stores and indexes the filtered data. It also improves Splunk’s performance and automatically implements indexing.
What is Splunk Enterprise?
Splunk Enterprise: Splunk enterprise components are the paid version with unlimited access to the IT businesses. Its architecture supports single and multi-site clustering for disaster recovery. Splunk Enterprise also gathers and analyzes the data from websites, applications, etc.
What is the process of parsing in Splunk?
Parsing – Since the Splunk software extracts the relevant data after examining, analyzing, and transforming the data, so this stage is also known as event processing. In this stage, the data stream is broken into individual events. Also, there are some sun-phases in the storage phase like: