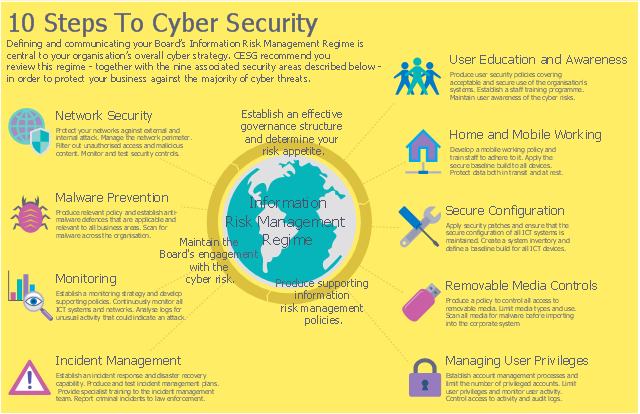
Examples of security incidents include the following: attempts from unauthorized sources to access systems or data; unplanned disruption to a service or denial of service;
What is a security incident response plan?
An incident response plan is a set of instructions to help IT staff detect, respond to, and recover from network security incidents. These types of plans address issues like cybercrime, data loss, and service outages that threaten daily work. A sufficient incident response plan offers a course of action for all significant incidents.
What is the definition of security incident?
Under the HIPAA Security Rule, a security incident is defined as: The attempted or successful unauthorized access, use, disclosure, modification, or destruction of information in an information system; or The attempted or successful unauthorized access, use, disclosure, modification or interference with system operations in an information system.
What is a security incident?
Security incidents are events that may indicate that an organization's systems or data have been compromised or that measures put in place to protect them have failed. In IT, a security event is anything that has significance for system hardware or software, and an incident is an event that disrupts normal operations.
What is an example of a cyber incident?
There are many different types of cyber incidents out there: A hacker gaining access to information that’s held within a secure corporate network Damage caused to a network system through the use of malware
What is an example of a security event?
What is the most common security incident?
What are some types of information security incidents?
- Third-Party Scanning. Scanning happens when an external group is doing reconnaissance or probing site security. ...
- Malware Infection. ...
- DoS Attacks. ...
- Unauthorized Access. ...
- Internal Security Breach. ...
- Privilege Escalation Attack. ...
- Advanced Persistent Threat.
What from the following are part of security incident?
What is potential security incident?
What are the 3 components of information security?
What are the 4 types of IT security?
- Critical infrastructure security.
- Application security.
- Network security.
- Cloud security.
- Internet of Things (IoT) security.
Which one is not the indication of security incident?
What is a physical security incident?
What is incident response in security?
Is tailgating a security incident?
How to detect security incidents
Nearly every day there's a new headline about one high-profile data breach or another. But there are many more incidents that go unnoticed because organizations don't know how to detect them.
Common attack vectors
An attack vector is a path or means by which a hacker can gain access to a computer or network server to deliver a payload or malicious outcome. Attack vectors enable hackers to exploit system vulnerabilities, including human operators.
Understanding the attackers methodology and goals
Although an organization can never be sure which path an attacker will take through its network, hackers typically employ a certain methodology -- i.e., a sequence of stages to infiltrate a network and steal data. Each stage indicates a certain goal along the attacker's path.
Mitigate the risk of the 10 common security incident types
There are many types of cybersecurity incidents that could result in intrusions on an organization's network:
Trends in the causes of incidents
According to the 2019 " Data Security Incident Response Report " by BakerHostetler LLP, a U.S. law firm, certain types of security incidents are on the rise.
Creating an incident response plan
The expanding threat landscape puts organizations at more risk of being attacked than ever before. As a result, enterprises must constantly monitor the threat landscape and be ready to respond to security incidents, data breaches and cyberthreats when they occur.
What is security incident?
security incident. An occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
What is an incident in computer security?
A violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices. See incident. An occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system;
What is a security breach?
An occurrence that actually or potentially jeopardizes the confidentiality, integrity, or availability of a system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies. ...
What is an imminent threat?
An occurrence that actually or imminently jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system; or constitutes a violation or imminent threat of violation of law, security policies, security procedures, or acceptable use policies.
What is the definition of security breach?
An occurrence that results in actual or potential jeopardy to the confidentiality, integrity, or availability of an information system or the information the system processes, stores, or transmits or that constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies.
What is the definition of "intentionally"?
An occurrence that actually or potentially jeopardizes, without lawful authority, the confidentiality, integrity, or availability of information or an information system; or constitutes a violation or imminent threat of violation of security policies, security procedures, or acceptable use policies. An occurrence that actually or potentially ...