Which of the following are fundamental objectives of information security? Confidentiality, Integrity, and Availability are the fundamental objectives of health information security and the HIPAA Security Rule requires covered entities and business associates to protect against threats and hazards to these objectives. Click to see full answer.
Which of the following are fundamental objectives of Health Information Security?
24/06/2020 · Which of the following are fundamental objectives of information security? Confidentiality, Integrity, and Availability are the fundamental objectives of health information security and the HIPAA Security Rule requires covered entities and business associates to protect against threats and hazards to these objectives. Click to see full answer.
What are the fundamentals of information security?
27/09/2021 · (1) The hatchet “information security” way protecting information and information equipment from unauthorized access, use, disclosure, disruption, modification, or damage in order come provide: A. Integrity , which means guarding against improper information modification or destruction, and includes ensuring details nonrepudiation, accuracy, and also …
What is an example of security objective?
28/02/2021 · Which of the following are fundamental objectives of information security? The CIA triad of confidentiality integrity and availability is at the heart of information security . ( The members of the classic InfoSec triad—confidentiality integrity and availability—are interchangeably referred to in the literature as security attributes properties ...
What are the 3 attributes of information security?
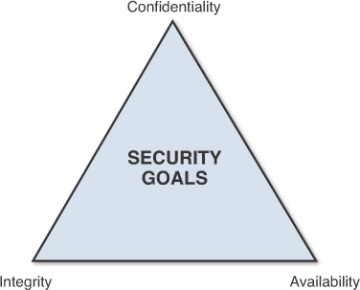
CIA Triad: The Fundamental Objectives Of Information Security. In the world of information security, we often hear the term “CIA Triad.” CIA represents something we strive to attain. It refers to confidentiality, integrity, and availability. These 3 are the unifying attributes of an information security program. Moreover, each of these attributes represents a fundamental objective of …
What are the 3 main objectives of information security?
When we discuss data and information, we must consider the CIA triad. The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability. Each component represents a fundamental objective of information security.
What are the fundamentals of information security?
What are the 3 Principles of Information Security? The basic tenets of information security are confidentiality, integrity and availability. Every element of the information security program must be designed to implement one or more of these principles. Together they are called the CIA Triad.
Which of the following is not the objective of information security?
3. Which is not an objective of network security? Explanation: The Identification, Authentication and Access control are the objectives of network security. There is no such thing called lock.
Which of the following is not one of the 3 fundamental aspects of information security?
The fundamental principles (tenets) of information security are confidentiality, integrity, and availability. Every element of an information security program (and every security control put in place by an entity) should be designed to achieve one or more of these principles.24-Jul-2020
What are the three types of security?
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.10-Jan-2020
What are the fundamentals of security army?
Successful security operations depend on properly applying five fundamentals:Provide early and accurate warning.Provide reaction time and maneuver space.Orient on the force or facility to be secured.Perform continuous reconnaissance.Maintain enemy contact.
Which is an objective of network security?
Network security entails protecting the usability, reliability, integrity, and safety of network and data. Effective network security defeats a variety of threats from entering or spreading on a network. The primary goal of network security are Confidentiality, Integrity, and Availability.
Which of the following is one of the cyber security goals?
Protect the confidentiality of data. Preserve the integrity of data. Promote the availability of data for authorized users.
Which of the following is a type of cyber security?
Hence, to provide security, it is divided into the following types: Cloud Security: Provides security for the data stored on the cloud. Network Security: Protects the internal network from threats. Application Security: Protects data stored in the application software.
What are the three fundamental elements of an effective security program for information systems?
These three, identification, authentication, and authorization– surely boosts an entity's IS. thus, answering the question, what are the three fundamental elements of an effective security program for information systems.
What are the 3 aspects of security define each of them?
These three letters stand for confidentiality, integrity, and availability, otherwise known as the CIA triad. Together, these three principles form the cornerstone of any organization's security infrastructure; in fact, they (should) function as goals and objectives for every security program.09-Jul-2019
What are the fundamental principles of security Mcq?
Explanation: The 4 key elements that constitute the security are: confidentiality, integrity, authenticity & availability.
What is information security?
The primary information security objective is to protect information assets against threats and vulnerabilities, to which the organization’s attack surface may be exposed. Taken together, threats and vulnerabilities constitute information risk. Ensuring that security objectives are met and risk mitigated will benefit an organization by contributing to: 1 Business continuity 2 Operational Efficiency 3 Cost Effectiveness
What is the primary objective of information security?
The primary information security objective is to protect information assets against threats and vulnerabilities, to which the organization’s attack surface may be exposed. Taken together, threats and vulnerabilities constitute information risk. Ensuring that security objectives are met and risk mitigated will benefit an organization by contributing ...
How to make a business case for information security?
1. Outline an Information Security Strategy. An effective strategy will make a business case about implementing an information security program. A description of security objectives will help to identify an organization’s security function.
What is the purpose of confidentiality?
Confidentiality – ensuring privacy is a crucial data security objective. Confidentiality involves restricting data only to those who need access to it. Encryption and setting passwords are ways to ensure confidentiality security measures are met.
What is a security policy?
Implementing a security policy will clearly identify the information assets and systems that your organization must protect. Policy should apply to physical, personnel, administrative and network security. Information security policy will set rules and expectations for users to protect information assets and systems.
Most relevant text from all around the web
Which of the following are fundamental objectives of information security? The CIA triad of confidentiality integrity and availability is at the heart of information security .
Disclaimer
Our tool is still learning and trying its best to find the correct answer to your question. Now its your turn, "The more we share The more we have". Comment any other details to improve the description, we will update answer while you visit us next time...Kindly check our comments section, Sometimes our tool may wrong but not our users.
What are the threats to availability?
The following are threats to availability: 1 Loss of processing ability due to natural disasters 2 Hardware failures 3 Programming errors 4 Human errors 5 Sickness, injury, or death of key personnel 6 DDoS attacks, as well as 7 Malicious codes
Why is confidentiality important?
Then use it for financial gain. That’s why confidentiality is important. And it keeps any critical information from unauthorized access or use.
What is the CIA triad?
CIA Triad: The Fundamental Objectives Of Information Security. In the world of information security, we often hear the term “CIA Triad.”. CIA represents something we strive to attain. It refers to confidentiality, integrity, and availability. These 3 are the unifying attributes of an information security program.
Do business owners like to disclose information?
Confidentiality. Most of us don’t like to disclose financial or health information to strangers. Likewise, business owners don’t like the idea of disclosing their business’ critical information. Especially to competitors or cybercriminals. Information is valuable.
What is the importance of confidentiality?
So, this is where confidentiality is essential. Confidentiality refers to the protection of information against unauthorized people and processes. Every organization must remember that criminals always look for ways. And they’re prepared to exploit weak spots.
What is the highest ideal of personal character?
Integrity . Integrity is one of the highest ideals of personal character. A person with integrity lives life according to a code of ethics. Therefore we can trust him to behave in certain ways for a certain situation. The same principle applies to information security. Integrity refers to the protection of information from intentional ...
What is the principle of integrity?
The same principle applies to information security. Integrity refers to the protection of information from intentional or accidental modification. Thus, you can rely upon that the information is the same as what it should be. Additionally, integrity applies both to data and the system.