What is a CMAC (CMAC)?
Cipher-based message authentication codes (or CMACs) are a tool for calculating message authentication codes using a block cipher coupled with a secret key. You can use an CMAC to verify both the integrity and authenticity of a message. A subset of CMAC with the AES-128 algorithm is described in RFC 4493. New in version 0.4.
What is HMAC used for In cryptography?
Like any of the MAC, it is used for both data integrity and authentication. Checking data integrity is necessary for the parties involved in communication. HTTPS, SFTP, FTPS, and other transfer protocols use HMAC. The cryptographic hash function may be MD-5, SHA-1, or SHA-256.
What is the difference between AES CMAC and HMAC?
To resume it, AES-CMAC is a MAC function. It can be seen as a special case of One-Key CBC MAC1 (OMAC1) which also a MAC function that relies on a block cipher (so AES in the present case). HMAC is also a MAC function but which relies on a hash function ( SHA256 for HMAC-SHA256 for example).
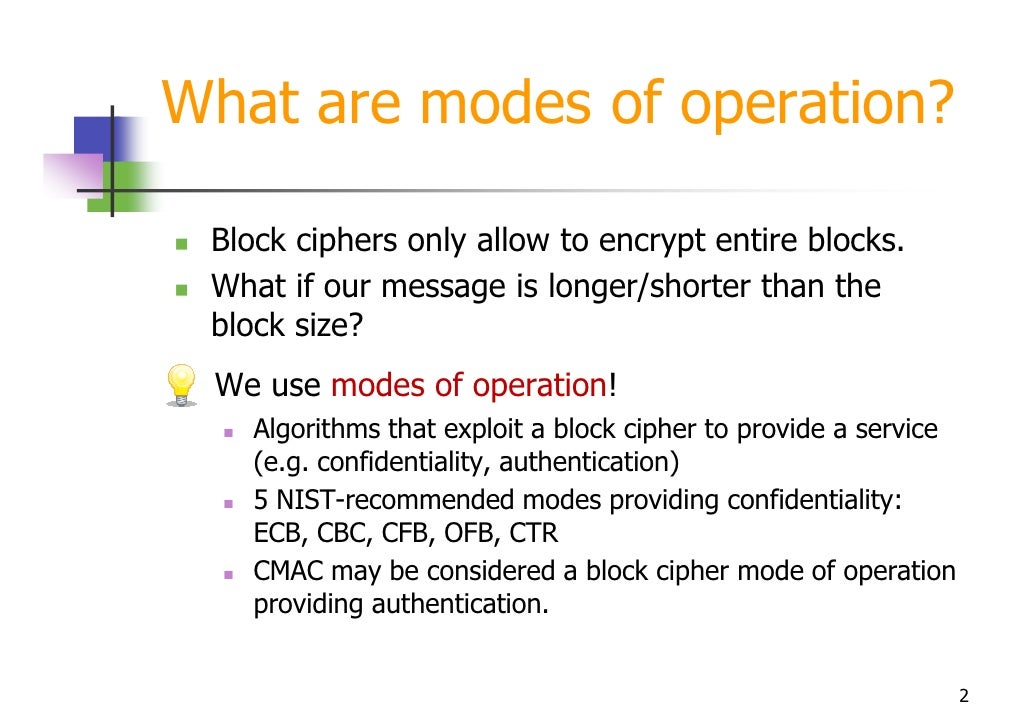
What is the OMAC1 equivalent to CMAC?
OMAC1 is equivalent to CMAC, which became an NIST recommendation in May 2005. It is free for all uses: it is not covered by any patents. In cryptography, CMAC is a block cipher -based message authentication code algorithm.
What is HMAC and CMAC in cryptography?
HMAC algorithm stands for Hashed or Hash-based Message Authentication Code. It is a result of work done on developing a MAC derived from cryptographic hash functions. HMAC is a great resistance towards cryptanalysis attacks as it uses the Hashing concept twice.
Is MAC and CMAC the same?
CMAC is a simple variant of the CBC MAC (Cipher Block Chaining Message Authentication Code). Whereas the basic CBC MAC is only secure on messages of one fixed length (and that length must be a multiple of the block size), CMAC takes and is secure across messages of any bit length.
What is difference between HMAC and CMAC?
Generally CMAC will be slower than HMAC, as hashing methods are generally faster than block cipher methods. In most cases HMAC will work best, but CMAC may work better where there is embedded hardware which has hardware accelleration for block ciphers. For this, CMAC would likely run faster than HMAC.
How many keys are used in CMAC?
MAC class (data operation keys): These keys are used to generate and verify MACs. The keys can be 128, 192, or 256 bits in length....MAC keys.DES keysCallable servicesMACVERCVV Key Combine, MAC Verify, Transaction Validation, VISA CVV Verify2 more rows
Which algorithm is used in CMAC?
7. Which cryptographic algorithm is used in CMAC? Explanation: The CMAC algorithm uses triple DES and AES.
What is CMAC number?
The CM MAC (Cable Modem MAC address) and Serial Number of your cable modem are printed on the bottom label.
What is the difference between MAC and MDC in cryptography?
Message detection code(MDC): The difference between MDC and MAC is that the second include A secrete between Alice and Bob. A modification detection code (MDC) is a message digest that can prove the integrity of the message: that message has not been changed.
Does HMAC use AES?
No. HMAC-SHA1 is very different from AES encryption. HMAC-SHA1 is not an encryption algorithm. It is a hashing function.
What is HMAC used for?
Hash-based message authentication code (or HMAC) is a cryptographic authentication technique that uses a hash function and a secret key. With HMAC, you can achieve authentication and verify that data is correct and authentic with shared secrets, as opposed to approaches that use signatures and asymmetric cryptography.
Is CMAC an encryption?
Cipher-based message authentication codes (or CMACs) are a tool for calculating message authentication codes using a block cipher coupled with a secret key. You can use an CMAC to verify both the integrity and authenticity of a message.
What is a MAC key?
The Mac's Control key is primarily for helping you “right-click” things, as described earlier. Instead, the Macintosh equivalent of the Windows Ctrl key is the ⌘ key. It's right next to the space bar.
What is HMAC key?
An HMAC key is a type of credential and can be associated with a service account or a user account in Cloud Storage. You use an HMAC key to create signatures which are then included in requests to Cloud Storage. Signatures show that a given request is authorized by the user or service account.
What is HMAC in a message?
What is HMAC (Hash based Message Authentication Code)? HMAC (Hash-based Message Authentication Code) is a type of a message authentication code (MAC) that is acquired by executing a cryptographic hash function on the data (that is) to be authenticated and a secret shared key. Like any of the MAC, it is used for both data integrity ...
What is HMAC in a server?
HMACs provides client and server with a shared private key that is known only to them. The client makes a unique hash (HMAC) for every request. When the client requests the server, it hashes the requested data with a private key and sends it as a part of request.
Why are HMACs important?
Advantages. HMACs are ideal for high-performance systems like routers due to the use of hash functions which are calculated and verified quickly unlike the public key systems. Digital signatures are larger than HMACs, yet the HMACs provide comparably higher security.
What is the difference between MAC and HMAC?
They are message encryption, Message authentication code, and hash functions. Major difference between MAC and hash (HMAC here) is the dependence of a key. In HMAC we have to apply the hash function along with a key on the plain text. The hash function will be applied to the plain text message.
Why use HMACs?
HMACs can be used for Internet of things (IoT) due to less cost. Whenever there is a need to reset the password, a link that can be used once is sent without adding a server state. It can take a message of any length and convert it into a fixed-length message digest.
How are digital signatures similar to HMACs?
Digital signatures are nearly similar to HMACs i.e they both employ a hash function and a shared key. The difference lies in the keys i.e HMACs use symmetric key (same copy) while Signatures use asymmetric (two different keys).
What is a HMAC?
In cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. As with any MAC, it may be used to simultaneously verify both ...
What is the HMAC algorithm?
Any cryptographic hash function, such as SHA-2 or SHA-3, may be used in the calculation of an HMAC; the resulting MAC algorithm is termed HMAC-X, where X is the hash function used (e.g. HMAC-SHA256 or HMAC-SHA3-512). The cryptographic strength of the HMAC depends upon the cryptographic strength of the underlying hash function, the size of its hash output, and the size and quality of the key.
How many passes does HMAC use?
HMAC uses two passes of hash computation. The secret key is first used to derive two keys – inner and outer. The first pass of the algorithm produces an internal hash derived from the message and the inner key. The second pass produces the final HMAC code derived from the inner hash result and the outer key.
What is HMAC authentication?
As with any MAC, it may be used to simultaneously verify both the data integrity and the authenticity of a message. HMAC can provide message authentication using a shared secret instead of using digital signatures with asymmetric cryptography.
How many bits does SHA 256 have?
For example, SHA-256 operates on 512-bit blocks. The size of the output of HMAC is the same as that of the underlying hash function (e.g., 256 and 512 bits in the case of SHA-256 and SHA3-512, respectively), although it can be truncated if desired. HMAC does not encrypt the message.
Who first published the HMAC?
The definition and analysis of the HMAC construction was first published in 1996 in a paper by Mihir Bellare, Ran Canetti, and Hugo Krawczyk, and they also wrote RFC 2104 in 1997.
Is HMAC MD5 a PRF?
HMACs are substantially less affected by collisions than their underlying hashing algorithms alone. In particular, in 2006 Mihir Bellare proved that HMAC is a PRF under the sole assumption that the compression function is a PRF. Therefore, HMAC-MD5 does not suffer from the same weaknesses that have been found in MD5.