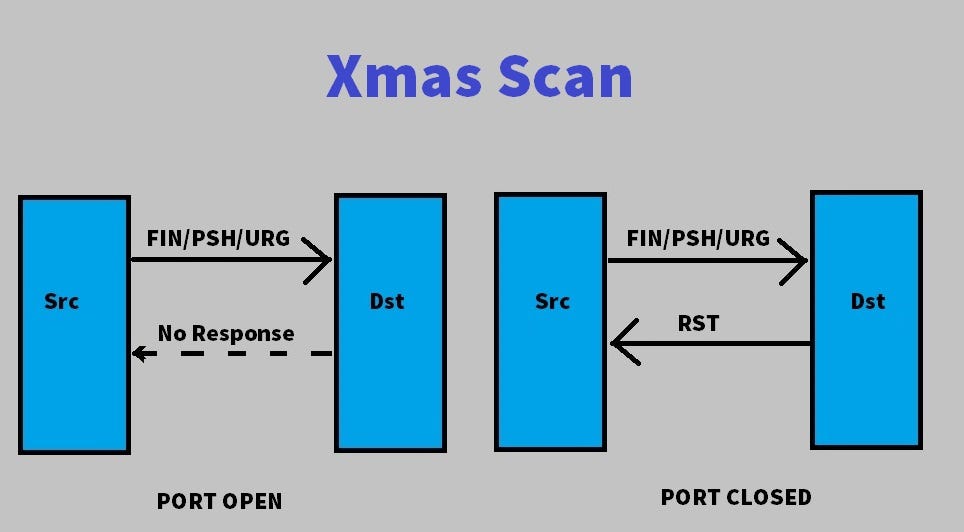
Xmas scans derive their name from the set of flags that are turned on within a packet. These scans are designed to manipulate the PSH, URG and FIN flags of the TCP header The Transmission Control Protocol (TCP) is a core protocol of the Internet protocol suite. It originated in the initial network implementation in which it complemented the Internet Protocol (IP). Therefore, the entire suite is commonly referred to as TCP/IP.Transmission Control Protocol
What are Xmas scans?
Since the Holidays are upon us, I thought it would be a good time to discuss Xmas Scans, also known as Christmas tree scans—the only network scan with a name that invokes thoughts of cookies, gifts and holiday joy. Xmas scans derive their name from the set of flags that are turned on within a packet.
What is Xmas scan in TCP?
These scans are designed to manipulate the PSH, URG and FIN flags of the TCP header. So in other words, the Xmas scan in order to identify listening ports on a targeted system will send a specific packet. Click to see full answer. Similarly one may ask, what is Xmas scan in nmap?
Does Xmas scan work on open ports?
If the port is open, there is no response; but if the port is closed, the target responds with a RST/ACK packet. XMAS scans work only on target systems that follow the RFC 793 implementation of TCP/IP and don’t work against any version of Windows.
What is the difference between Xmas scan and fin scan?
XMAS scans work only on target systems that follow the RFC 793 implementation of TCP/IP and don’t work against any version of Windows. FIN- A FIN scan is similar to an XMAS scan but sends a packet with just the FIN flag set. FIN scans receive the same response and have the same limitations as XMAS scans.
What is the purpose of port scanning?
A port scan is a common technique hackers use to discover open doors or weak points in a network. A port scan attack helps cyber criminals find open ports and figure out whether they are receiving or sending data. It can also reveal whether active security devices like firewalls are being used by an organization.
How does nmap perform Christmas scan?
Nmap Xmas Scan can be performed using nmap -sX command.
What is an Xmas scan quizlet?
Xmas scan. In the Xmas scan, Nmap sends packets with URG, FIN, and PSH flags activated. This has the effect of "lighting the packet up like a Christmas tree" and can occasionally solicit a response from a firewalled system. Not all systems will respond to probes of this type.
How do you detect a fin scan?
Depending upon the method used it may be necessary to sniff the network in order to see the response. FIN scans are detected via heuristic (non-signature) based algorithms, much in the same way as other scan types are detected. An IDS/IPS system with heuristic algorithms is required to detect them.
What is stealth scan?
Stealth scans Stealth scan types are those where packet flags cause the target system to respond without having a fully established connection. Stealth scanning is used by hackers to circumvent the intrusion detection system (IDS), making it a significant threat.
What does the flag do in an Nmap scan?
Add in the -A flag on your Nmap command, you can discover the operating system information of the hosts that are mapped. The -A flag can be used in combination with other Nmap commands. Using the -O flag on your Nmap command will reveal further operating system information of the mapped hosts.May 14, 2019
Which of the following attacks are more difficult to detect?
Insider attacks still far more difficult to detect and prevent than external cyber attacks. A recent survey conducted by Gurucul of more than 320 IT security experts, found that 15 percent of people said they would delete files or change passwords upon exiting a company.Jul 8, 2019
Which Nmap flag can be used for Xmas tree scan?
Xmas scan ( -sX ) Sets the FIN, PSH, and URG flags, lighting the packet up like a Christmas tree.
How does a SYN scan work quizlet?
How does a SYN scan work? In a normal TCP session, a packet is sent to another computer with the SYN flag set. The receiving computer sends back a packet with the SYN/ACK flag set, indicating an acknowledgment.
What type of scan is a FIN scan?
FIN SCAN is one of the port scanning methods in Nmap, which uses the sheer stupidity of old and stateless firewalls. In fact, when it comes to FIN Scan, our Port Scanner software sends a packet with a flag in the form of FIN meaning the end of the session to the destination firewall or host.
What is missing from a half open scan?
A half open does not include the final ACK - a threeway handshake is part of every TCP connection and happens at the beginning of every connection. In the case of a half-open scan, however, a final ACK is not sent, therefore leaving the connection halfway complete.
How does FIN scan work?
The FIN scan sends a packet that would never occur in the real world. It sends a packet with the FIN flag set without first establishing a connection with the target. If a RST (reset) packet is received back from the target due to the way the RFC is written, the port is considered closed.Jul 5, 2016
What is a nmap Xmas scan?
Nmap Xmas scan was considered a stealthy scan which analyzes responses to Xmas packets to determine the nature of the replying device. Each operating system or network device responds in a different way to Xmas packets revealing local information such as OS (Operating System), port state and more. Currently many firewalls and Intrusion Detection System can detect Xmas packets and it is not the best technique to carry out a stealth scan, yet it is extremely useful to understand how it works.
Is the Xmas scan new?
While the Xmas scan isn’t new and most defense systems are capable to detect it becoming an obsolete technique against well protected targets it is a great way of introduction to uncommon TCP segments like PSH and URG and to understand the way in which Nmap analyzes packets get conclusions on targets. More than an attack method this scan is useful ...
What is a Xmas scan?
What is Xmas scan in nmap? Nmap Xmas scan was considered a stealthy scan which analyzes responses to Xmas packets to determine the nature of the replying device. Each operating system or network device responds in a different way to Xmas packets revealing local information such as OS (Operating System), port state and more.
Is a FIN scan the same as a XMAS scan?
FIN scans receive the same response and have the same limitations as XMAS scans. NULL - A NULL scan is also similar to XMAS and FIN in its limitations and response, but it just sends a packet with no flags set.
Port States
Timing Templates
- Paranoid: -T0, extremely slow, useful to bypass IDS (Intrusion Detection Systems) Sneaky: -T1, very slow, also useful to bypass IDS (Intrusion Detection Systems) Polite: -T2, neutral. Normal: -T3, this is the default mode. Aggressive: -T4, fast scan. Insane:-T5, faster than Aggressive scan technique.
Nmap Xmas Scan Examples
- The following example shows a polite Xmas scan against LinuxHint. Example of Aggressive Xmas Scan against LinuxHint.com By applying the flag -sVfor version detection you can get more information on specific ports and distinguish between filtered and filtered ports, but while Xmas was considered a stealth scan technique this addition may make the scan more visible to firewa…
Conclusion
- While the Xmas scan isn’t new and most defense systems are capable to detect it becoming an obsolete technique against well protected targets it is a great way of introduction to uncommon TCP segments like PSH and URG and to understand the way in which Nmap analyzes packets get conclusions on targets. More than an attack method this scan is useful ...